¶ VergeIO Networks
VergeIO Networking is versatile, with each Network(vNet) acting as a virtual switch at Layer 2, with the option to include router as well and manage Layer 3 management capabilities within VergeIO, including: firewall, NAT/PAT, routing, dhcp, DNS, throttling, diagnostics and traffic monitoring.
¶ External Networks
The VergeIO External Network is what is used to connect to pre-existing networks created outside of VergeIO. For example: your corporate LAN or WAN, or a dedicated Internet connection. A single VergeIO system can have multiple External Networks. You can connect an External Network using any of the following methods:
- Direct connection
- vLAN
- vxLAN
- OSPF
- BGP
¶ Internal Networks
Every Internal Network is created default-secure, which means it is completely isolated from all other networks until Network Rules are created to open up inbound and / or outbound access as needed. This helps to avoid inadvertent security vulnerabilities.
NOTE: VMs within the same network are not firewalled from each other.
¶ Examples:
¶ Example 1
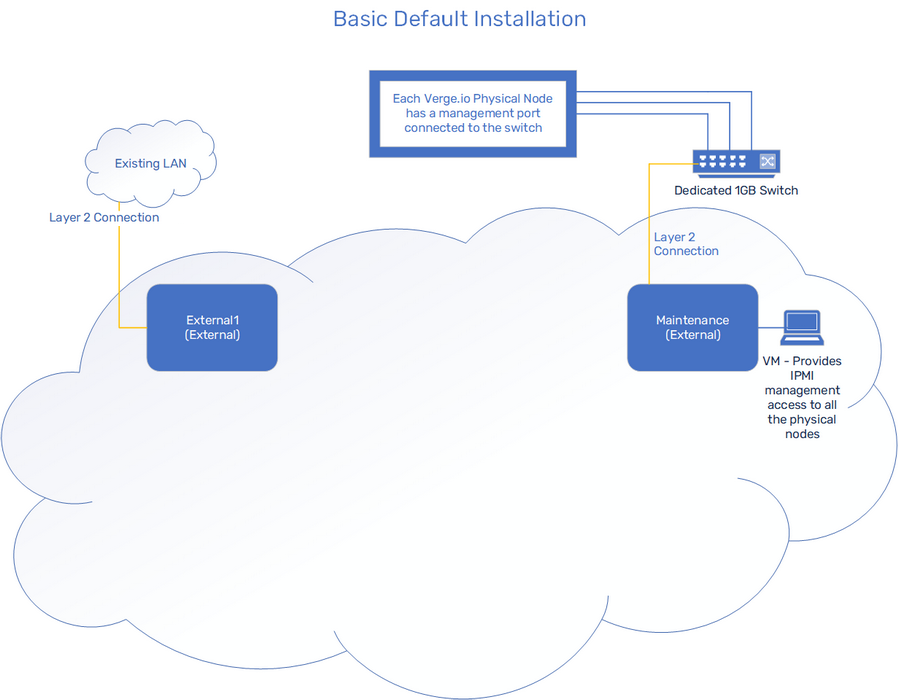
This example shows a standard configuration created by installation creating 2 External Networks:
External-LAN, the first External Network, is connected to an existing corporate LAN with a 10Gb uplink, tagged for vLAN 10.
Maintenance, the second External Network is connected to a dedicated, isolated 1Gb switch that is used for IPMI access to all the physical nodes. We can attach a VM to this network that we can use to access the management interface or console of all the physical nodes.
¶ Example 2
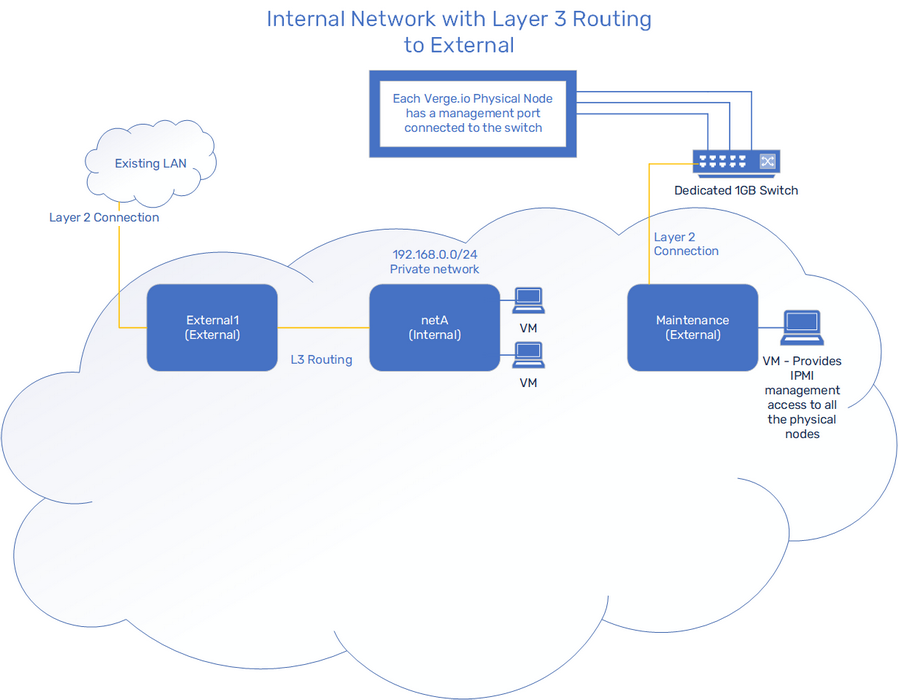
In Example 2, we build on the previous example and add one Internal Network. This network is private but we create Rules to control inbound/outbound traffic from the outside world and only allow needed traffic.
netA is an Internal Network and is assigned the default IP Address of 192.168.0.1. It is created default-secure, meaning that originally it is completely isolated; Rules can be created to explicitly route, firewall and NAT to allow only the desired traffic.
¶ Example 3
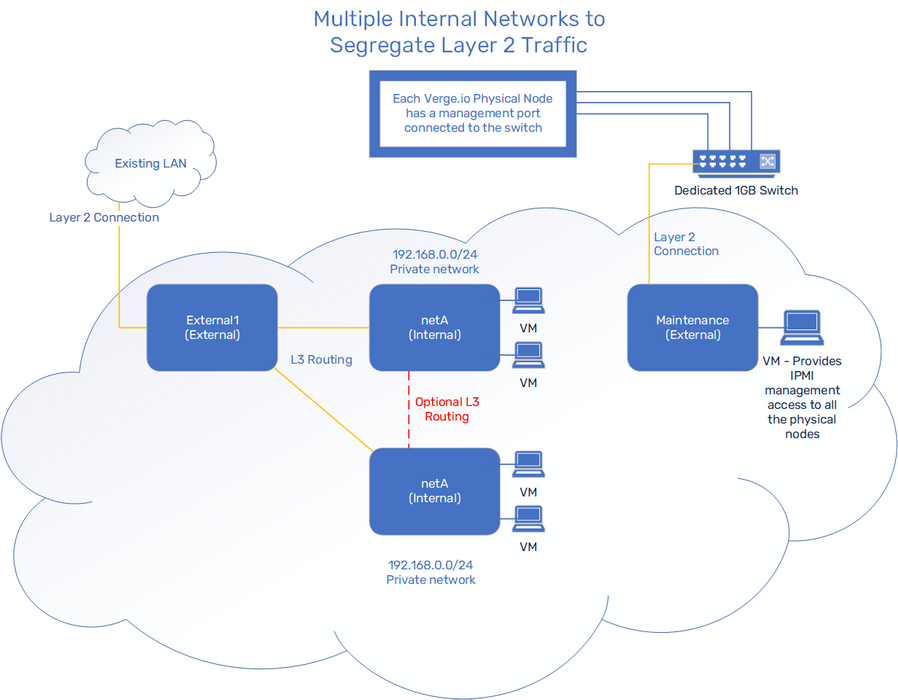
In Example 3, we have high traffic within our Internal VMs, so we want to break up the Layer 2 traffic. In order to segregate Layer 2 traffic, we utilize 2 separate Internal Networks. Both internal networks are configured to route traffic through External1 as needed. Routes can optionally be created to allow Layer 3 communication between our Internal networks.
2 Internal Networks, each with separate routes through External1
¶ Example 4
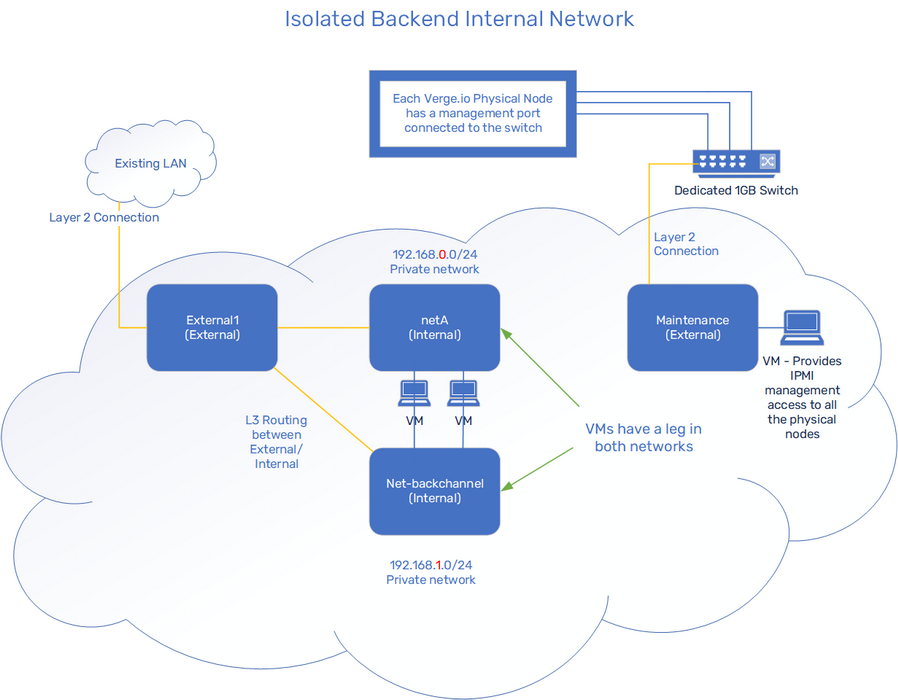
In the above example, each of our VMs is connected to 2 Internal Networks: one that has routing through the External and one that is kept completely isolated; this provides a separate backend communication channel for the Virtual Machines; this can accommodate various software clustering solutions, e.g. Rancher, Kubernetes, etc.
2 Internal Networks:
- One Network has Layer 3 routing to / from External Network.
- One Network is kept isolated from the External
Need more Help? Email [email protected] or call us at (855) 855-8300