¶ How to create an IPSEC VPN tunnel in VergeIO
In VergeIO, the DMZ Network is where the basic routing between networks is handled.
- Every router has a NIC and an IP address in the DMZ. This is how traffic transverses from network to network inside the VergeIO platform.
- Each vNet is its own VXLAN or VLAN.
These instructions are for setting up the IPsec Tunnel to connect to a VergeOS Internal Network. If you are connecting the tunnel to an External Network or have a special use case, the network rules below will have to be adjusted to accomodate those changes.
- Reserve a static IP address on the Internal (LAN) network which will be used by the VPN connection on that network. In this example, an IP address of 192.168.0.254 was set to static on the internal network named Internal.
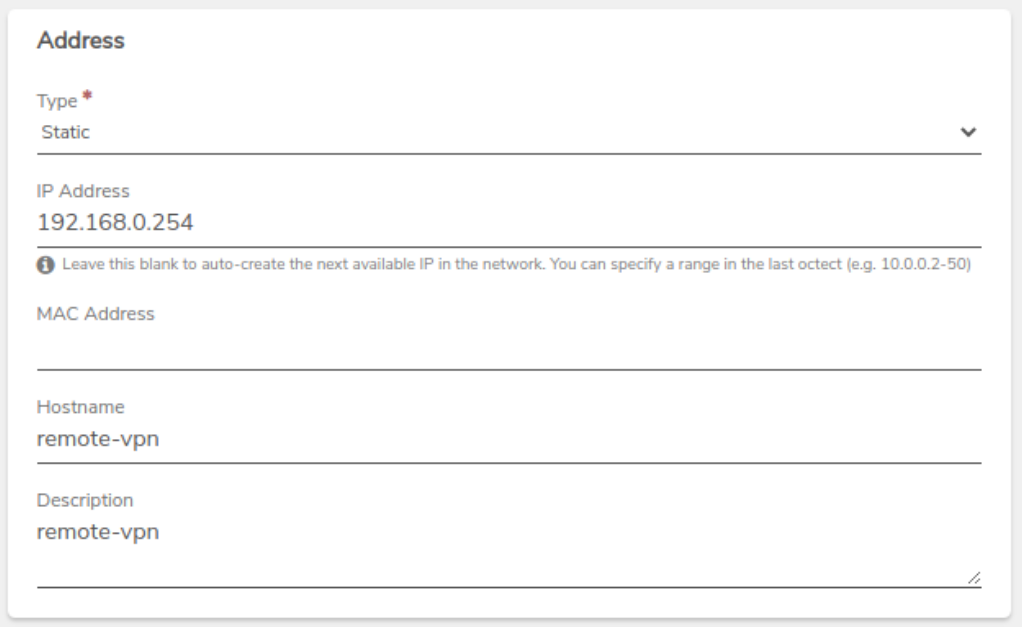
- For Type, set to Static.
- For IP Address, choose one of the available IP addresses in the system. If there are no unused IP addresses, an additional IP will need to be added.
- Navigate to Main Dashboard > Networks and click New VPN on the left menu.
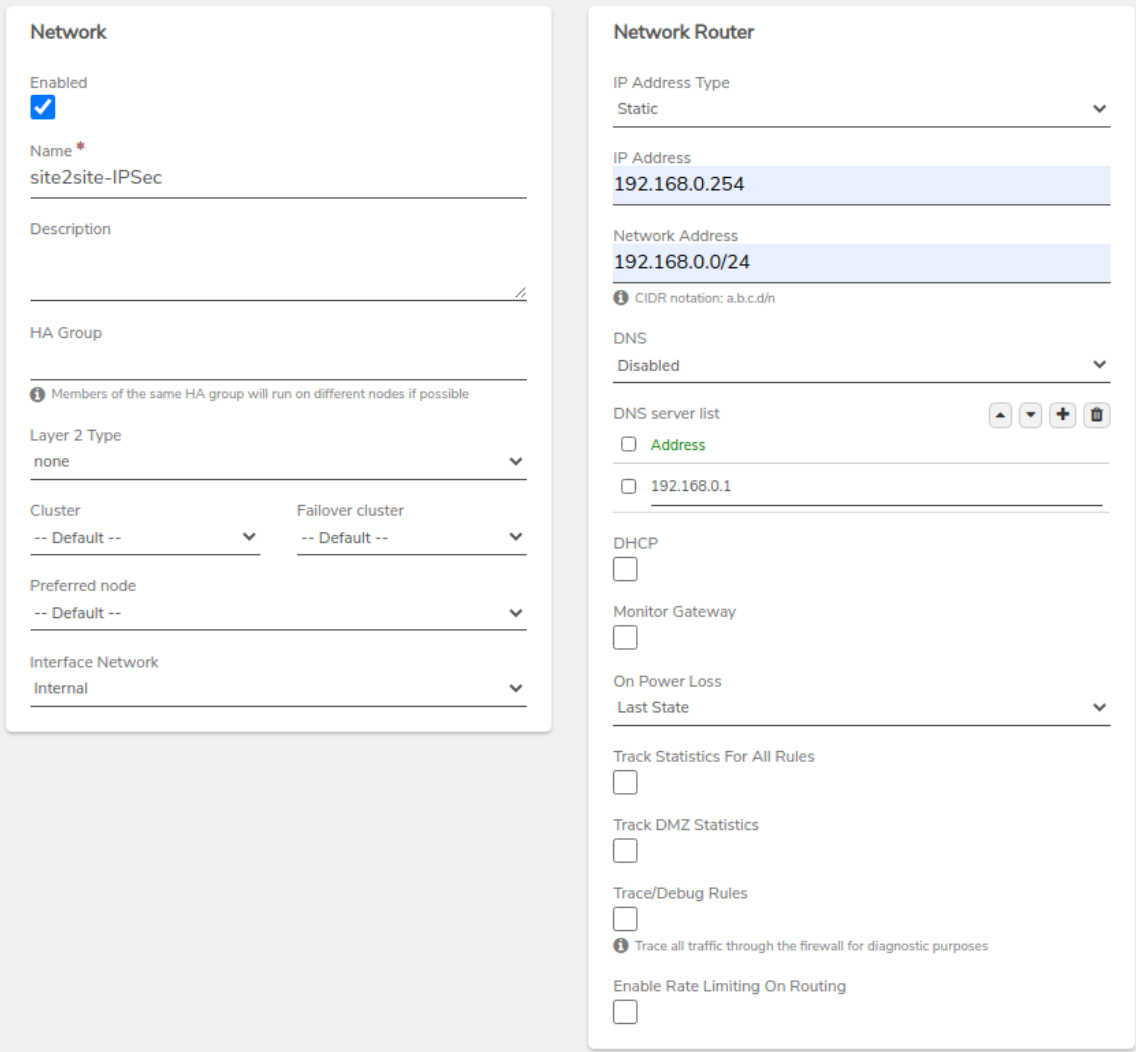
These settings are variable based on each connection but are important to define.- For Network, Layer 2 - configure as required by the connection.
- For Network, Interface Network - Select the network being bridged to the VPN Connection.
- For Network, set the IP Address Type** to Static.
- For Network Router, IP Address - Enter the IP address reserved in Step 1.
- From the newly created VPN Dashboard, click on Edit IPSec to edit the configuration if necessary to add/update connection-specific information.
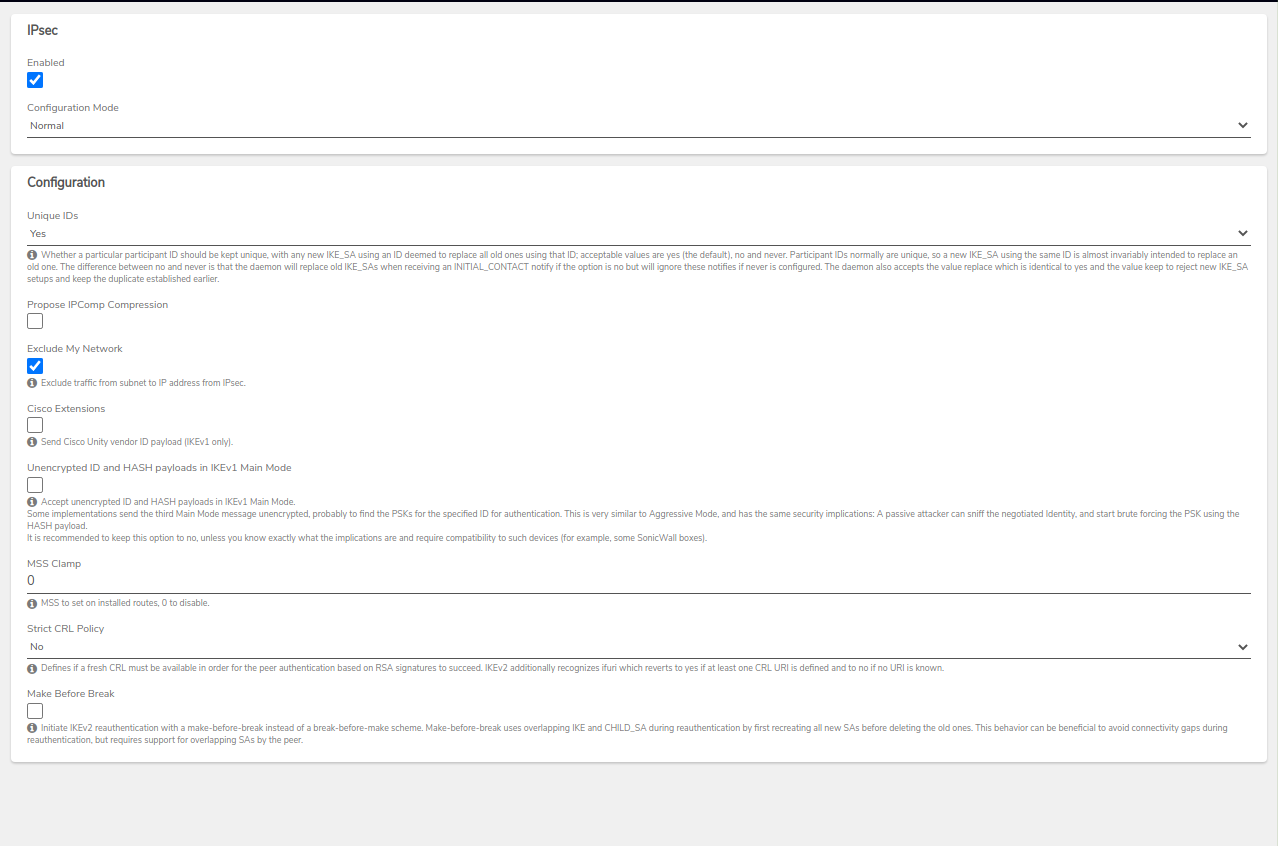
-
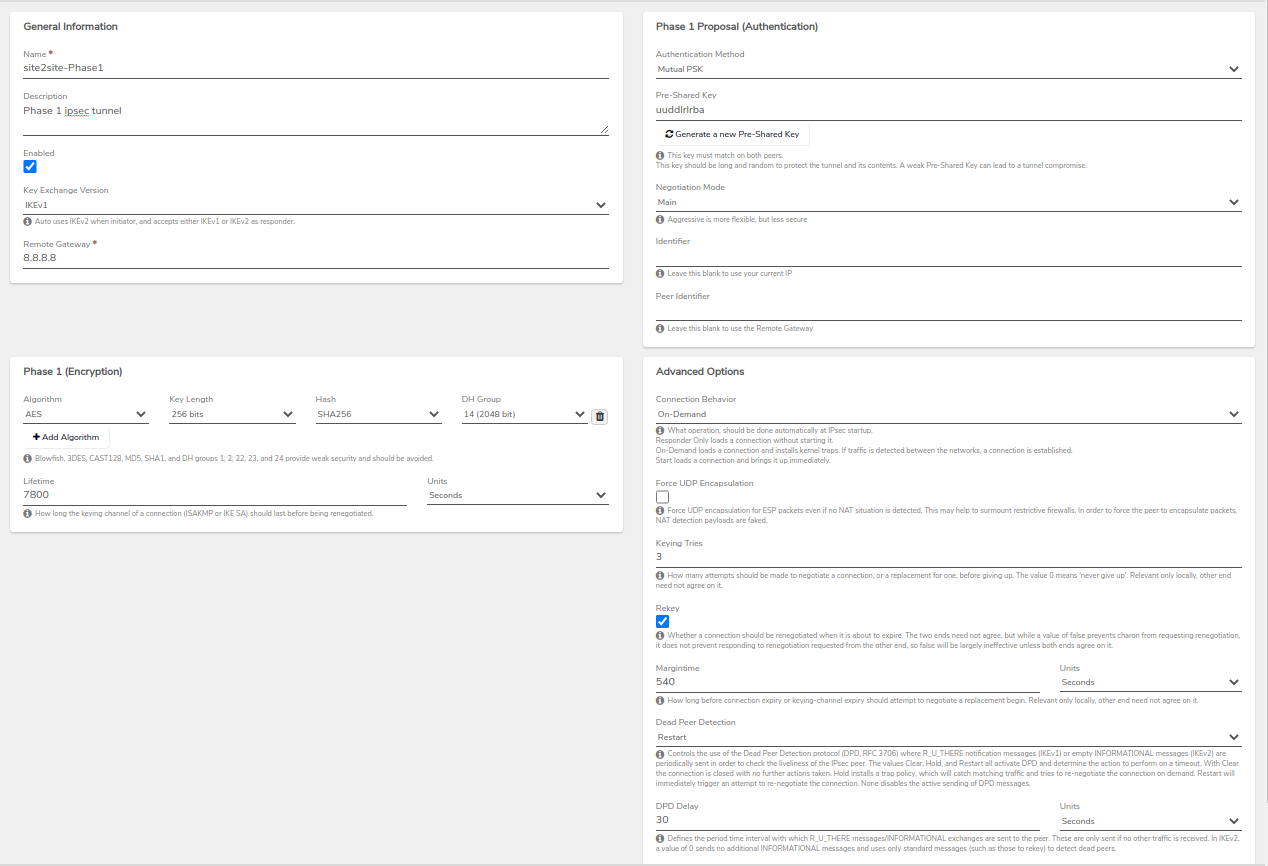
Click on IPSec Tunnels to start creating the IPSec Tunnel between the Verge.io environment and the remote site.
- For Remote Gateway - configure as required by the connection.
- For Phase 1 Proposal (Authentication), define the Authentication Method and Pre-Shared Key with connection-specific information.
-
When completing the Phase 1 setup, you will automatically be launched to configuring Phase 2.
If navigating manually, navigate to Main Dashboard > Networks Dashboard > VPNs > VPN Connection> Phase 1s. Highlight the Phase 1 created previously, and click ‘View P2s’- For Mode, set to Tunnel.
- For Local Network, configure as required by the connection.
- For Remote Network - configure as required by the connection.
- For Phase 2 Proposal, configure as required by the connection.
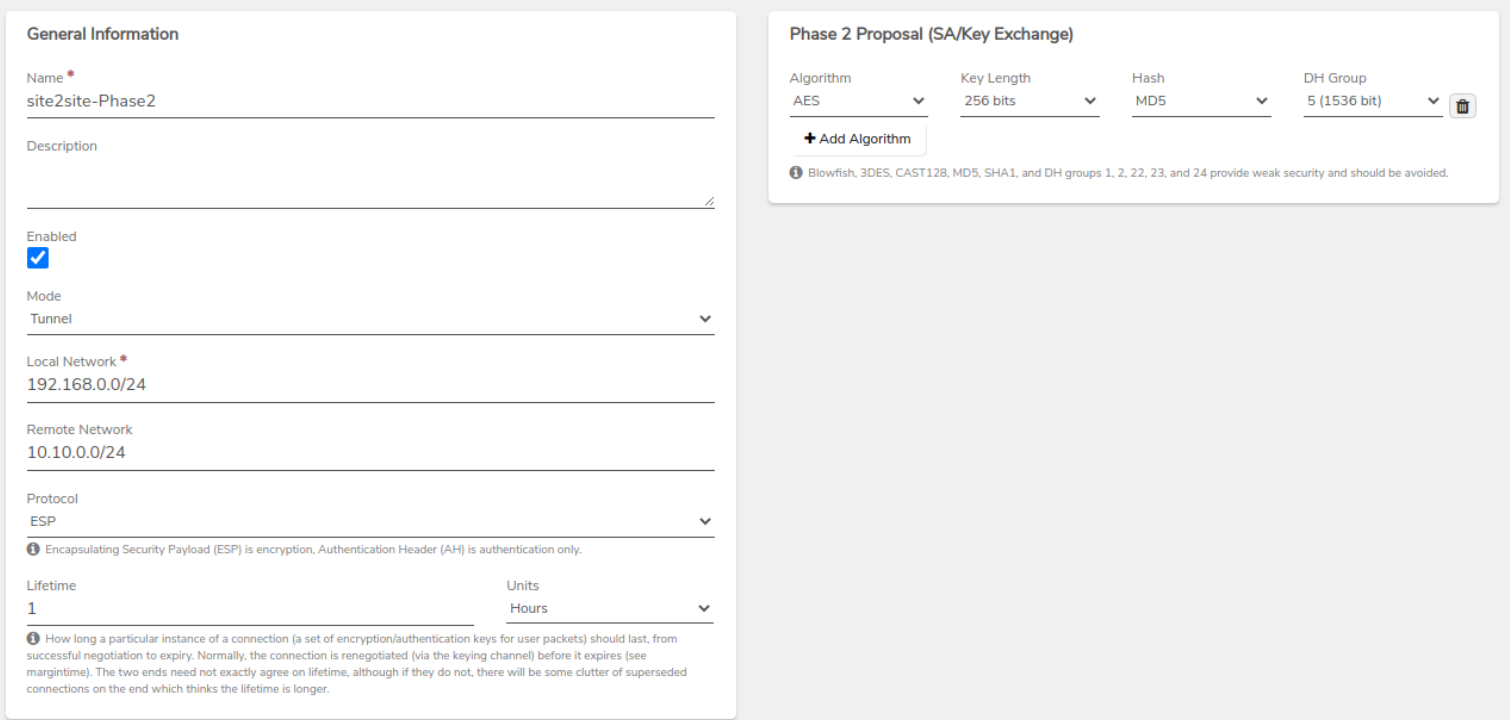
NOTE: This will automatically create rules on the VPN network.
-
VPN Network Rules - Review the rules to verify their configuration.
- Accept incoming, named Allow IKE, Protocol UDP, Destination IP: My Router IP, Port: 500
- Accept incoming, named Allow IPSEC NAT - Traversal, UDP, Destination IP: My Router IP, Port 4500
- Accept incoming, named Allow ESP, Protocol ESP, Destination IP: My Router IP
- Accept incoming, named Allow AH, Protocol AH, Destination IP: My Router IP
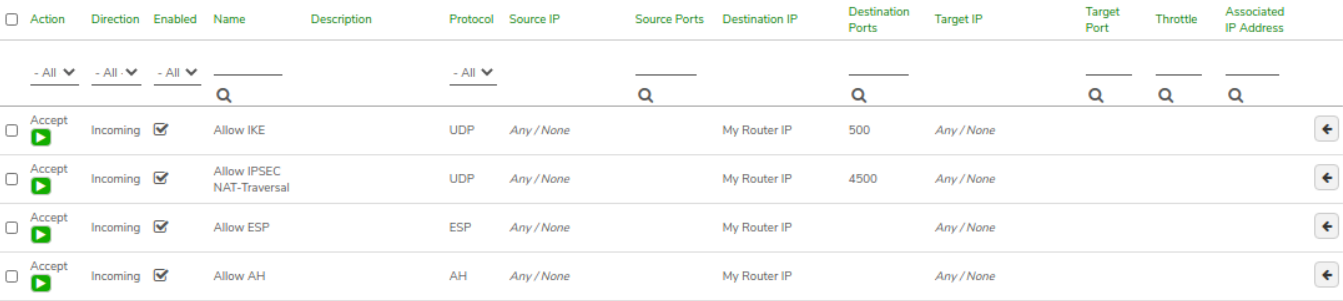
-
External Network Virtual IP Assignment - Assign a new virtual IP to the new VPN network from the External network. This will be the Public side of the VPN tunnel.
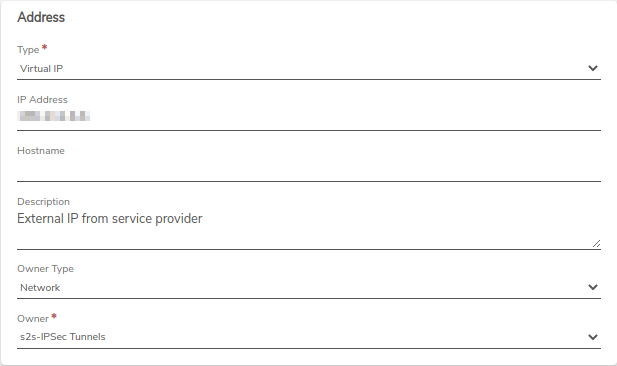
- VPN Network Rule - This will automatically create an outgoing route rule on the VPN network with that virtual IP address, which will have to have the rule applied. Verify that the rule is present and then Apply Rules to save the changes.
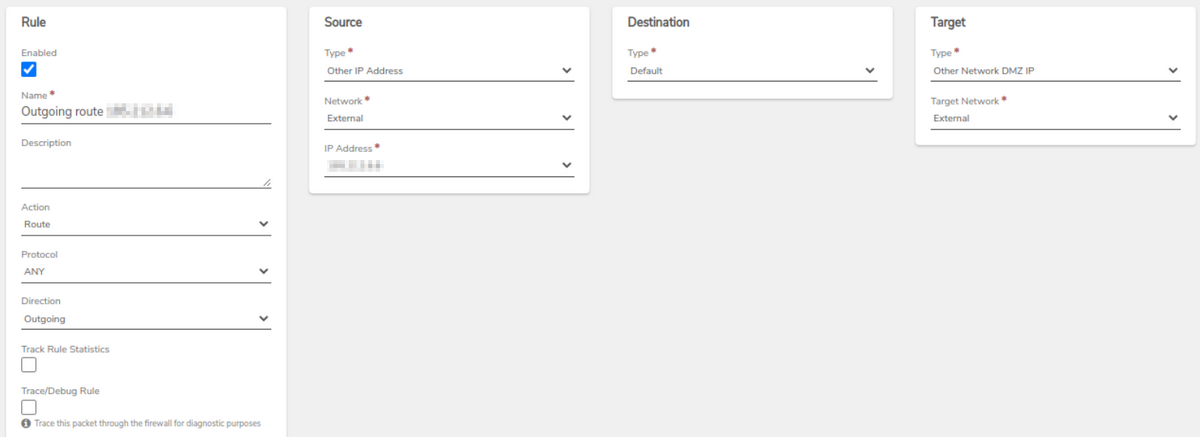
- VPN Network Rule - This will automatically create an outgoing route rule on the VPN network with that virtual IP address, which will have to have the rule applied. Verify that the rule is present and then Apply Rules to save the changes.
-
VPN Network Rule - Create a Default Route rule for the new VPN network to define the default path outbound for traffic inside this network.
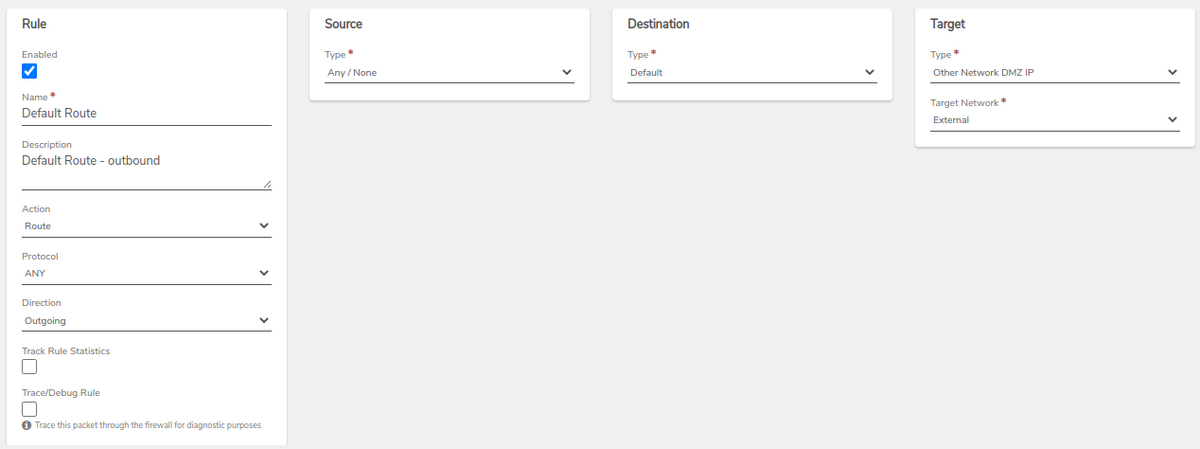
-
VPN Network Rule - Create an sNAT rule on the new VPN network to mask external traffic
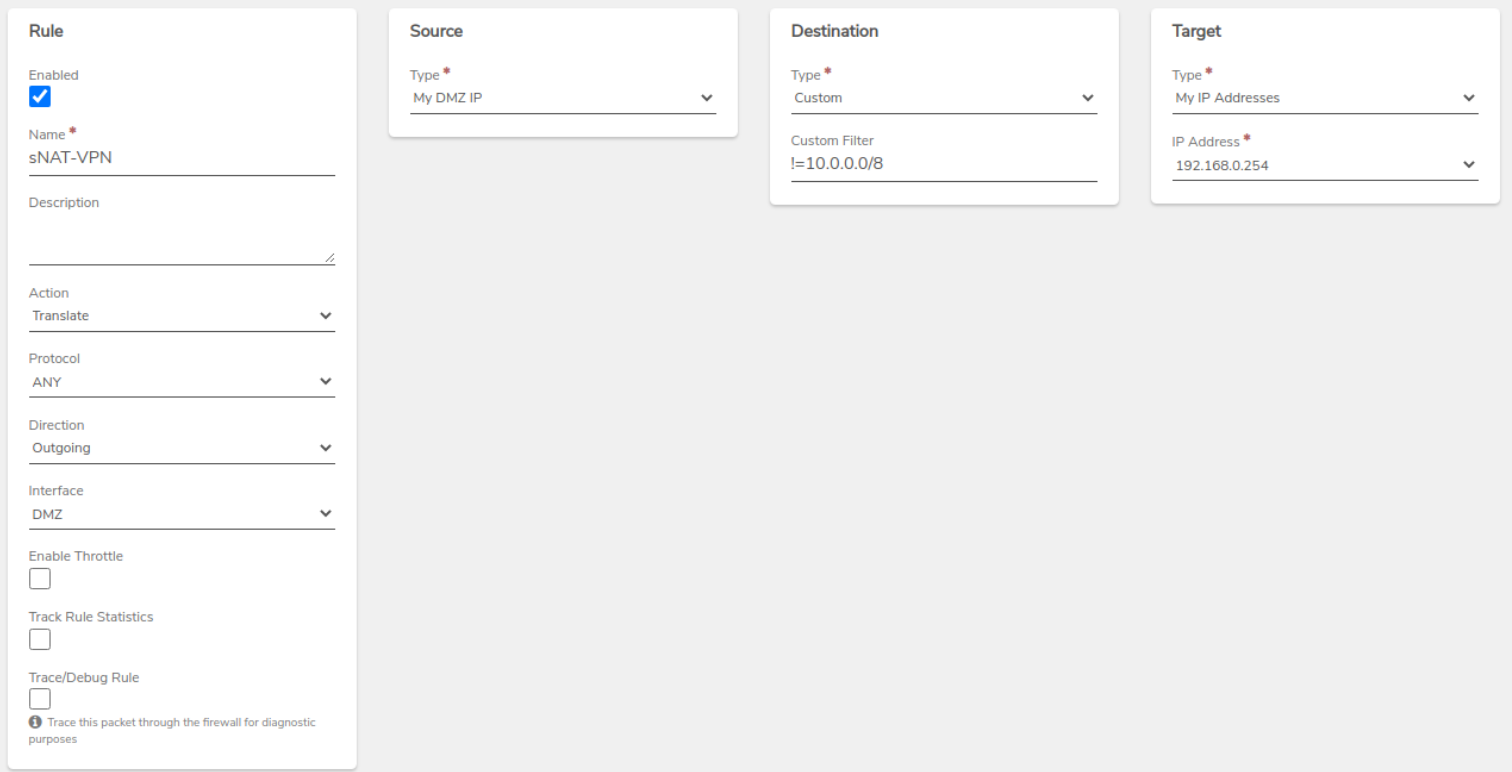
-
VPN Network Rule - Create a general sNAT rule to work as a catchall for traffic from this network.
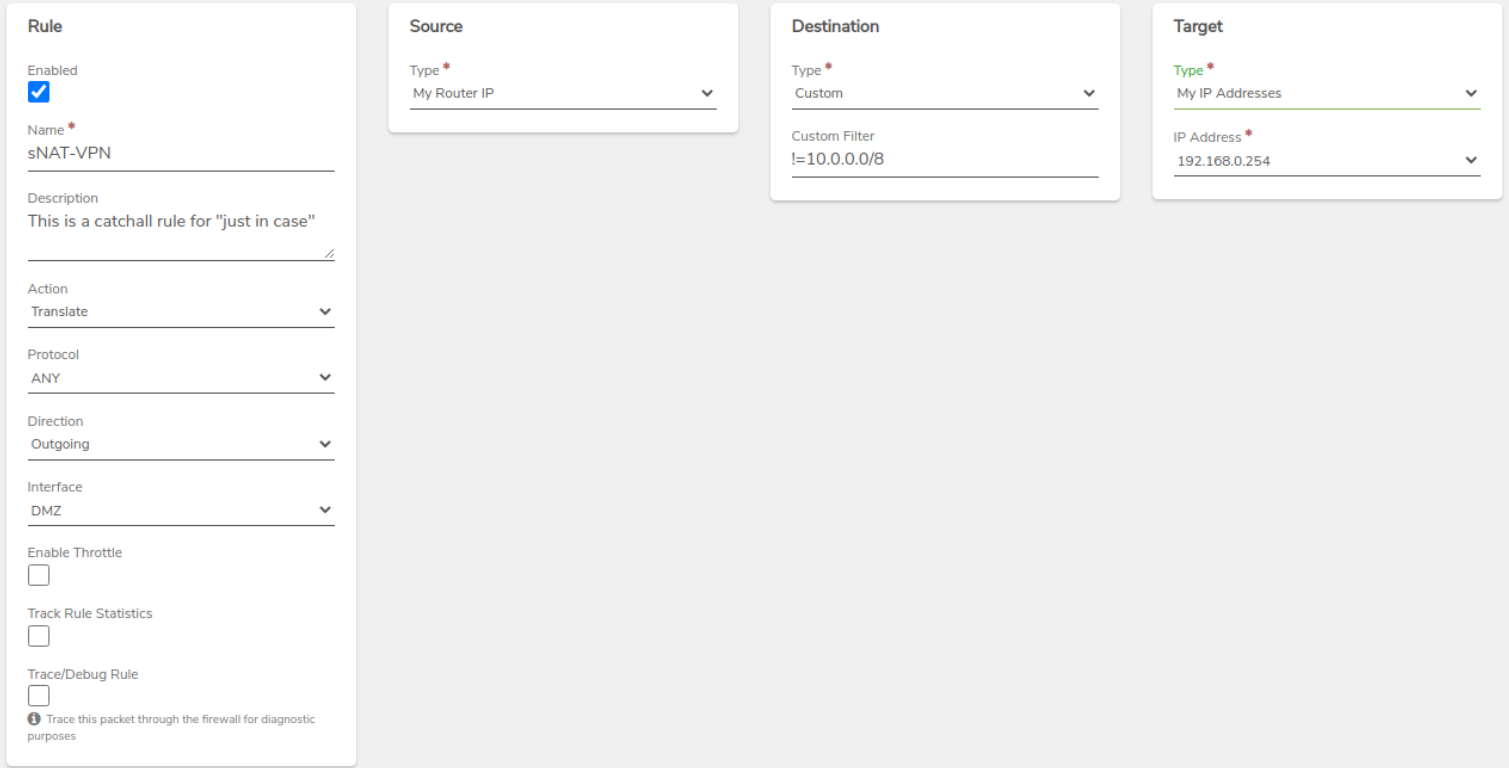
-
VPN Network Rule - Create a new Translate rule to allow traffic from the VPN tunnel to access this network.
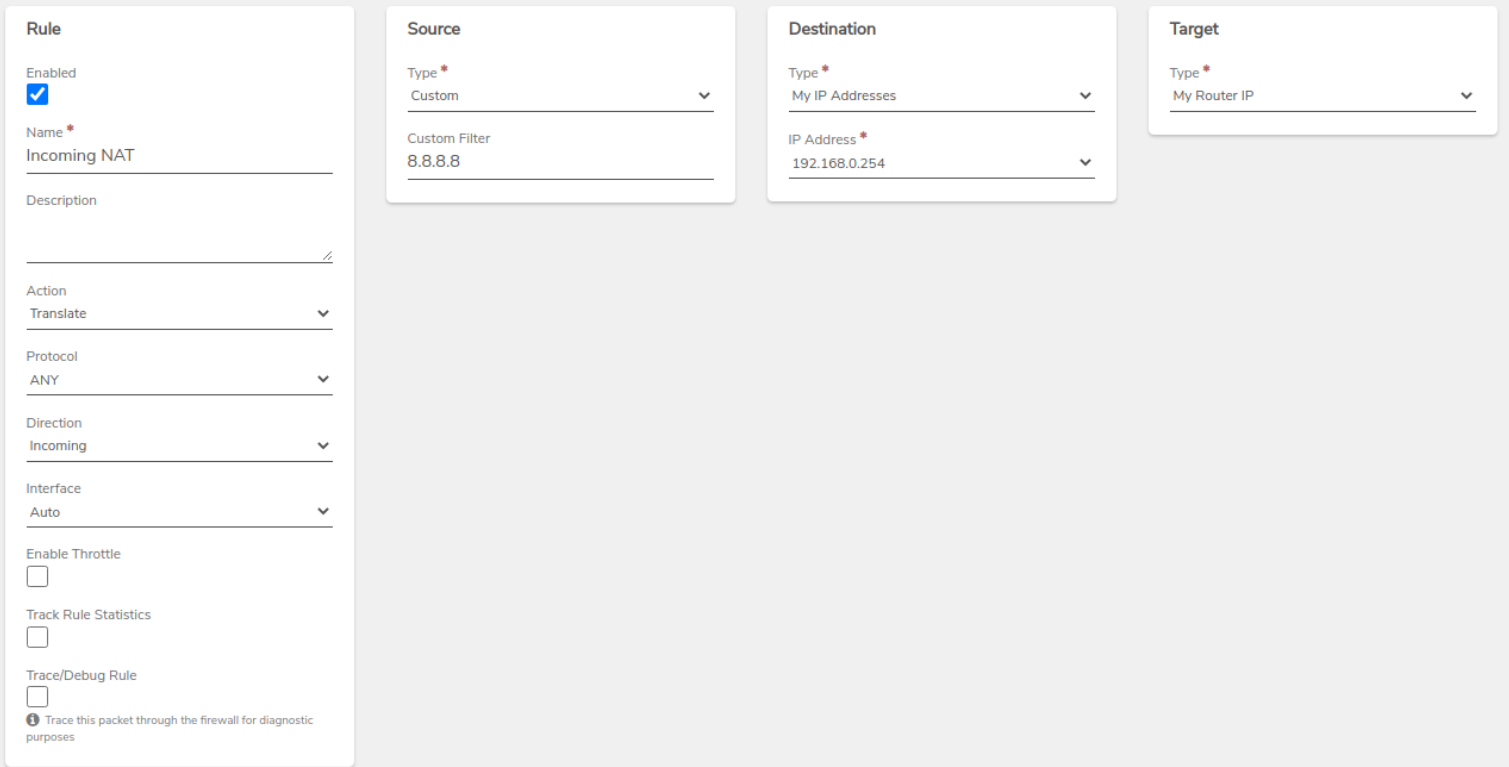
-
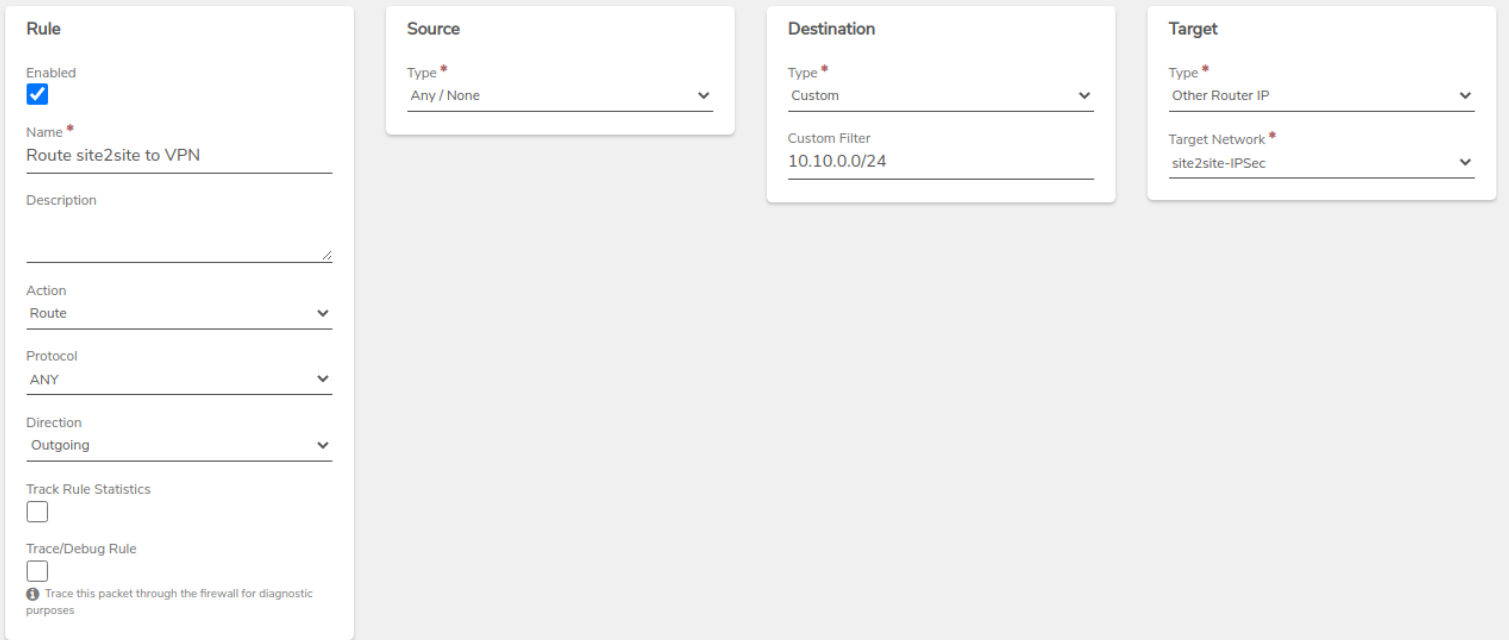
VPN Network Rule - Create a new accept rule on the VPN network to allow traffic from the remote network incoming.
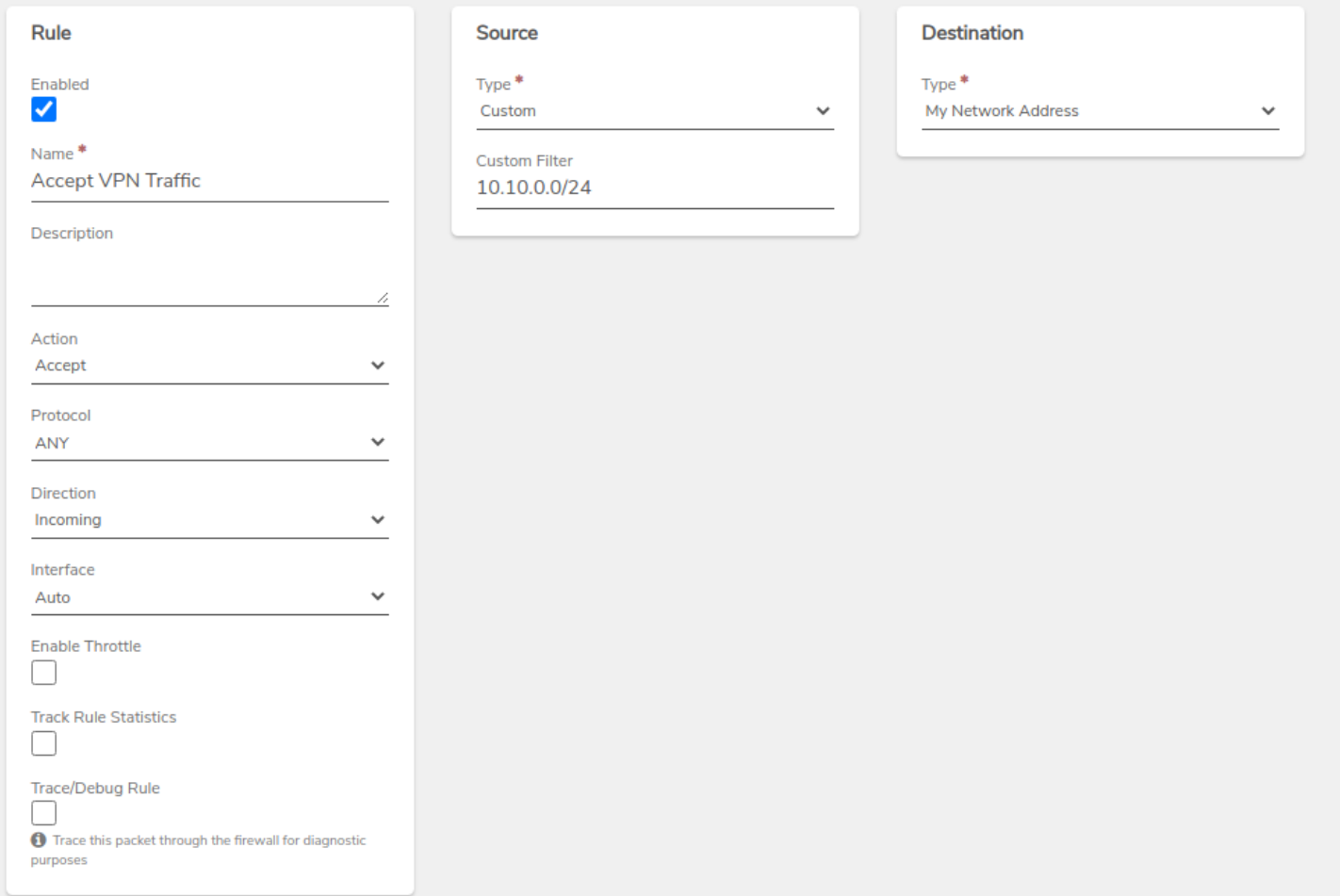
-
VPN Network Rule - Create a new accept rule on the VPN network to allow traffic
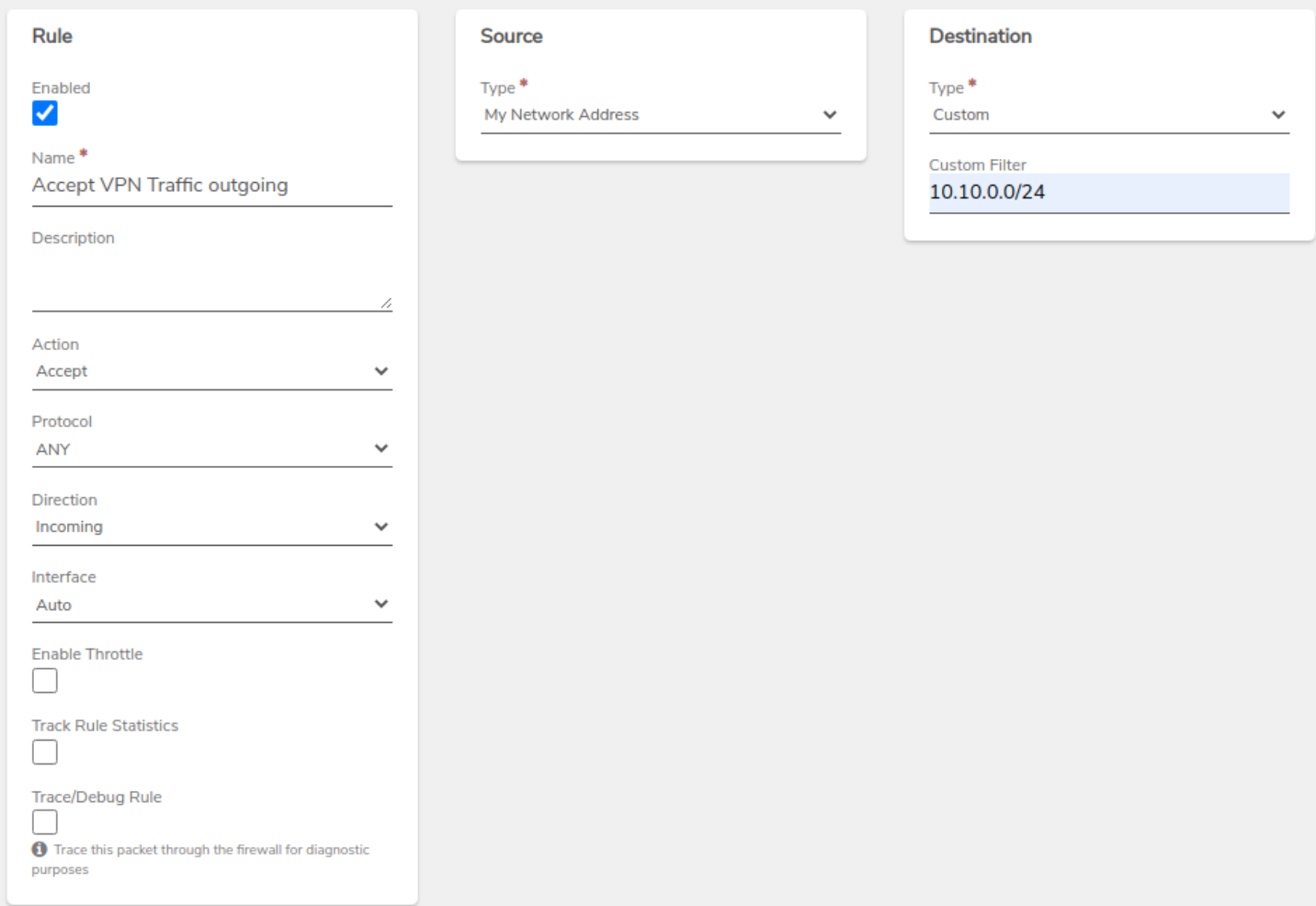
-
Internal Network Rule - Create a new route rule on the internal network to send traffic properly out of the VPN tunnel.
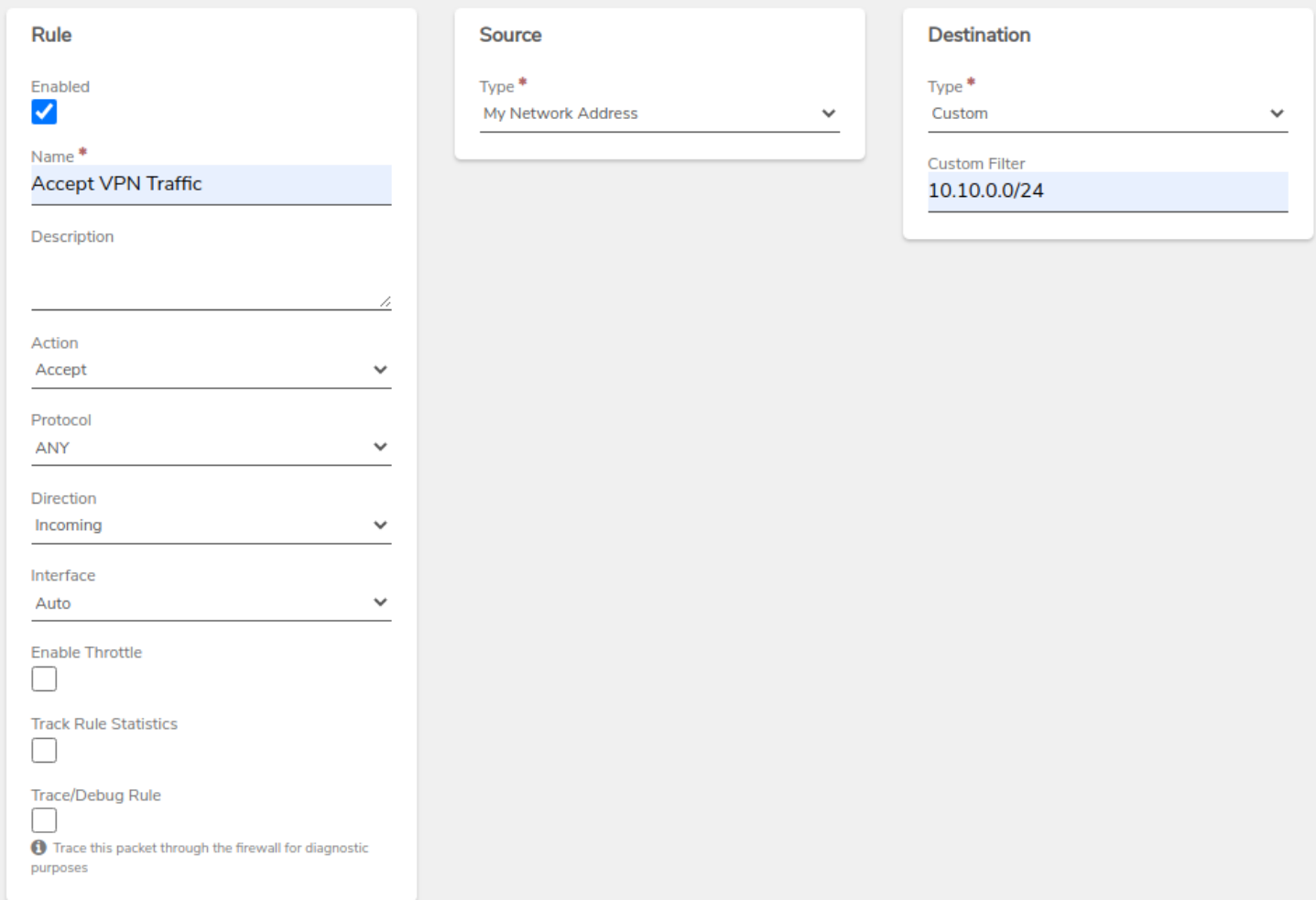
-
Internal Network Rule - Create a new accept rule on the internal network to allow traffic from the remote network.
¶ Connecting to IPsec
- Open the VPN network's Dashboard (Networks->VPNs then double-click on the Network).
- Scroll down to the IPsec Connections section and click the plug icon to connect.
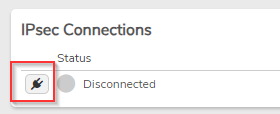
- Watch for the IPsec status to show connected. If it doesn't, continue on to the next step.
¶ Troubleshooting Guide
This guide will take you through some common testing and diagnostic tools to help troubleshoot why the IPsec VPN is not working.
¶ Checking Logs/Status
Logs will not be shown in the VPN logs section for the IPsec connection. These are shown in diagnostics.
- Click on Diagnostics on the left menu.
- Change the Query to Logs and click Send.
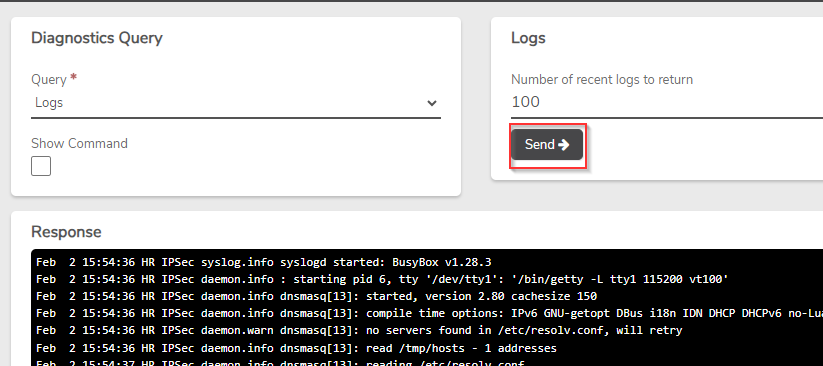
- Scroll down to the latest logs at the bottom and review the errors.
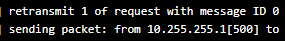
- The most common cause of issues is not able to connect to the tunnel as you can see above it will retry.
¶ Connection issues
If you are receiving a bunch of retransmit messages then you may be having connection issues. Most commonly this is caused by incorrect network rules or firewall setups. Below is a common list of things to check.
- Click on Diagnostics on the left menu.
- Change the Query to Ping.
- Change the Host to the IP of the VPN network's Remote Gateway.
- Hit Send and look for packet failures.
If you are not able to ping the Remote Gateway then you have something blocking your connection or a missing route. This is also assuming that the gateway is responding to pings, confirm this by pinging the Remote Gateway outside of VergeOS.
¶ Other things to check
- Test if you can ping 8.8.8.8, this will tell you if you have internet on this network. If you can't, confirm that you have a Default Route in your Rules.
- Run the diagnostic query "What's My IP". Assuming your VPN is over the WAN, you should get a response.
- Run a diagnostic TCP Connection test to the Remote Gateway on the IKE port (default 500). This is assuming your firewall has TCP and UDP allowed on that port, if you are only allowing UDP incoming then this will fail anyway but a lot of times both are open and it's a good test.
- Run a diagnostic Trace Route to the Remote Gateway. Check that the traffic is routing correctly. If not, look at your Default route rules in the VPN and External networks.
- Run a diagnostic IPsec with Status All. This will give you the current state of the IPsec Tunnel. You can also change this to Show Config and review the config for accuracy.
- Check for other logs in the Diagnostics Logs. You can change the results to show more than 100 lines if needed.
Need more Help? Email [email protected] or call us at (855) 855-8300